WHY YOU SHOULD USE A SECURITY OPERATIONS CENTER WITH AI, MACHINE LEARNING & AUTOMATION CAPABILITIES
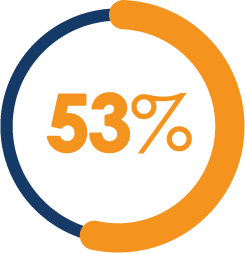
Research shows that a majority of organizations (53%) are dissatisfied with the current state of their Security Operations Center (SOC), citing that it’s ineffective at investigating, gathering evidence and detecting the source of threats.
If you currently operate a SOC, do you share those sentiments? If you don’t have one in place, these insights might be enough to deter you from the idea altogether.
The reality is that a SOC can help centralize and optimize your security efforts. The only caveat? The level of support you need might expand beyond what your in-house team can provide.
That’s when it pays to partner with a managed services provider who can help alleviate the burden and take your SOC initiatives to the next level. Today, we’re sharing the ins and outs of our Managed SOC solution and the doors it can help open for your enterprise.
READY TO LEARN MORE? LET’S GET STARTED.
WHAT IS A SOC? WHAT DOES IT MEAN?
A SOC, is a facility that houses a team of dedicated, skilled and trained information security personnel. This team is responsible for monitoring the real-time status of your security posture on a continuous, ongoing basis. Rather than attending to countless disparate duties, a SOC’s goal is to detect, analyze, defend, investigate and report cybersecurity issues either before they occur, or as soon as they arise.
To do so, they will leverage a high-tech set of tools and processes, keeping a constant eye on the activity going on across your:
- Networks
- Servers
- Endpoints
- Applications
- Databases
- Websites
- Other critical systems
A SOC team, solely focused on the security operations center, and comprised of security analysts, engineers and managers, has the necessary expertise and knowledge needed to effectively respond to activities potentially linked to a security compromise.
WHY IS A SOC IMPORTANT?
In short, a SOC helps you close the gap between the time a potential compromise occurs and how long it takes your enterprise to detect and respond to it. Your IT department might follow industry best practices to help curb the risk of cyber threats and keep your enterprise as secure as possible. Yet, no in-house approach can take the place of having a team of personnel wholly dedicated to security incident detection.
A SOC team can continuously monitor and analyze your organization’s data activity around the clock, on a 24/7 basis. This way, if a threat comes in on a weekend, or in the middle of the night, you can still respond. You’re always protected, regardless of the time or type of attack.
HOW CAN YOU MONITOR IT SECURITY DEPARTMENT ACTIVITIES?
While monitoring security operations is critical to ongoing business security and success, most organizations don’t have the capacity, resources or budget needed to establish a separate SOC to handle these tasks.
That’s where we come in. Through our Managed SOC offering, we can set up a SOC at our location staffed by industry experts that are trained in the latest threat intelligence capabilities and completely focused on your organization.
This frees up your teams from pulling double duty or being pulled in a million different directions. It also strengthens your security efforts, so you can focus on the mission-critical tasks that keep your company running on a daily basis.
When you let us take the reins, you’ll maintain full visibility and control of your security operations. The only difference? When you outsource the security operations center to us, we cut out the noise. You can make clearer and more informed security decisions because you’ll only need to focus on the true security events we detect.
THE POWER OF CENTRALIZED VISIBILITY
With EI, your IT security department activities go from scattered to centralized. Rather than searching different devices and checking various endpoints, you’ll find all your security events automatically organized into one comprehensive dashboard with the help of our Digital Robotics Engine (DRE).
Using widely-proven algorithms, this artificial intelligence (AI) engine correlates all security events identified in every security application across your entire enterprise. Then, it sorts through them and displays only the ones that fall outside of the typical user patterns that its detected for your organization.
Not only is this layout more visually appealing, but it’s more accurate. While we believe our team is the best in the security business, relying on manpower or human effort alone can weaken your security infrastructure. Instead, automation helps ensure validity, so you never have to worry about a potential threat slipping through the cracks. Let’s take a closer look at how AI can enhance and improve your SOC initiatives.
WHAT IS THE ROLE OF AI IN SECURITY OPERATIONS?
Across industries, AI is heralded for its ability to streamline business processes, eliminate cumbersome manual tasks, improve service quality and reduce operating costs. This holds true in the security realm, as well.
Our DRE tool uses AI and machine learning to understand your systems inside and out. From there, it can address any issues quickly and accurately to protect your monitoring and response systems from catastrophic failure.
THE VALUE OF METADATA
As the Digital Age continues to advance, networks are becoming more sophisticated. They’re also creating more data and exposing themselves to more threats than ever before.
As such, it can be impossible for a team of humans to sort through all of this information and monitor it for any anomalies, especially when the mountain of data grows at a constant rate. Conversely, an AI-driven security solution can breeze through that data based on established machine learning standards. Then, it transforms the unstructured insights into valuable metadata that drives real results.
Rather than examining unstructured data on a piece-by-piece basis, it sets up guidelines of normalcy and highlights any that fall outside this realm. Then, it uses predictive analysis to anticipate similar events before they arise.
As our DRE hunts for threats, it makes them instantly visible to a team of human remediators. Our AI tools are designed to enhance the functionality of our SOC team, enhancing their capabilities and improving their threat detection efforts. This helps our team understand the real nature of attacks, and lowers the amount of time spent responding to false positives.
HOW DOES AUTOMATION REDUCE MANAGED SERVICE COSTS?
At their core, automation and machine learning technologies are designed to help offset some of the burdens that humans bear. At the same time, they provide accelerated capabilities driven by advanced technologies that surpass human intelligence.
As they do so, they provide the following cost-savings benefits:
- Reduced operational times
- Maximized productivity
- Optimized resources
- Reduced risk of error
- Improved system recovery time
All these help to lower the overall cost of SOC operations, so you’re not wasting valuable resources on steps that aren’t furthering your security efforts.
WHAT ARE THE ADVANTAGES OF MANAGED SECURITY SERVICES?
 Why should you outsource your SOC efforts to us?
Why should you outsource your SOC efforts to us?
Because this is what we’re designed to do. While security might be top of mind for your organization, you have other fires to put out, customers to keep happy and project deadlines to meet.
On the other hand, we’re only focused on security, every hour of the day.
Our trained and experienced EI SecOps team will monitor your security status right from within our recently renovated, completely secure SOC. Depending on the level of service you require, we can staff our SOC to be on hand 24x7x365.
Next, let’s review a few other key benefits you’ll reap when you take this step.
MINIMIZED COSTS
A managed SOC allows you instant access to a team of seasoned security experts that work for you. All of this support is available at a fraction of what it would cost your organization to build your security team in-house.
The expenses associated with building a full stack of security technologies are enormous. From penetration testing and configuration management to security engineering and project management, these solutions are varied, and each is pricey. Plus, you can’t forget about the payroll and facility costs associated with hiring and housing this dedicated team.
A managed SOC solution allows you to reap the benefits of these solutions without their associated back-end costs. This makes it a more affordable solution in the long run.
RAPID INCIDENT RESPONSE
Whether you’re facing a single-stem compromise or an enterprise-wide intrusion, you need an incident response strategy that can quickly handle it all. Our Managed SOC solution gives you visibility into every facet of your security operations.
We’ll also cut out the noise by sorting and organizing threats for you through our advanced threat intelligence assessment. This way, you don’t waste any time determining if they are valid or not. Instead, you’re ready to act exactly when and where needed.
GLOBAL SECURITY REACH
Security threats don’t cease to exist when you travel. If you’re relying on your in-house team to communicate threats to you via traditional means, time zone and geographical differences could render that effort impossible, leading to potentially disastrous delays.
Our global reach and accessible platform make it easy for you to receive the notifications you need, regardless of where in the world you might be. Our DRE works in tandem with our SecOps team to provide full accessibility.
You can access your security dashboard at any time, from anywhere, on any device, so you’re always abreast of every situation as it arises.
SECURITY LOG INSIGHTS
Our Managed SOC solution doesn’t just help you identify and respond to cybersecurity threats on a case-by-case basis. We also deliver comprehensive reports and issue logs that can add additional value and insights. Within this documentation, you can identify trends and patterns that are out of your organization’s realm of normalcy.
Your dashboard will display these metrics, updating them as changes occur. This way, you can take a closer look at where threats are originating, common tactics used and other potential areas of vulnerability.
In this way, our Managed SOC solution ties in seamlessly with our Managed Security Information and Event Management (SIEM) solution. The latter can help correlate data and logs from various sources, generating automatic notifications about specific threats.
HOW CAN YOU ENHANCE YOUR SOC?
Looking to enhance the functionalities of your SOC? The answer lies in machine learning and automation.
If you’re still relying on legacy systems and in-house manpower to identify, correlate and respond to threats, you could be putting your organization at a significant disadvantage. Cyber attacks are becoming more advanced and likewise, so should your approach to enterprise-wide security.
When you invest in a Managed SOC solution, you can take your strategy to the next level. We’ll leverage state-of-the-art technology to improve, automate and quicken your security efforts so you’re always one step ahead of any attackers.
HOW CAN YOU REDUCE SECURITY BREACHES IN YOUR ORGANIZATION?
According to a recent study, 61% of organizations say they cannot identify breach attempts today without the use of modern, AI technology. In turn, 48% of respondents plan to increase their cybersecurity-related AI budgets by an average of almost 30% in the next year.
The old threat-detection approach of “trust but verify” is quickly falling by the wayside. As the threatscape continues to grow in scale and sophistication, reducing vulnerabilities means establishing a zero-trust security framework.
Machine learning algorithms help companies detect malicious activity and stop attacks before they even occur. In addition, the insights they provide can also help strengthen analysts’ job efforts, including:
- Analyzing the network
- Detecting attacks
- Protecting endpoints
- Assessing vulnerabilities
Reducing security breaches centers on an expert staff equipped with the tools and technologies required to provide the highest level of system monitoring possible. When you adopt machine learning solutions, you can push past human limitations, reduce errors, and improve the speed and accuracy of your response efforts.
LEVERAGE THE POWER OF A MANAGED SOC
Organizations are doing more and more business digitally every day, and as that occurs, threats to the safety and security of critical assets, data, and businesses as a whole, will continue to rise – as too will the attempts by cybercriminals to steal or corrupt them.
As the sophistication and regularity of their attacks grow, you’ll need to mount a heavy defense to help ensure their efforts are unsuccessful – and with regulations also becoming more burdensome, your security operations center will need to be knowledgeable, advanced and flexible enough to keep pace with evolving changes.
But for many organizations, limited resources for information security can restrict the ability to effectively manage their security operations. Fortunately, a Managed SOC with Enterprise Integration can simplify your security operations and increase your capabilities through the use of advanced tools and technologies. We’ll also provide you with all the benefits of a dedicated SOC at a fraction of the cost of hiring a full SOC staff.
VISIT OUR WEBSITE NOWto discover how easily you can boost the effectiveness of your security operations while lowering your operating costs.DON’T WAIT!Ensure the security of your organization’s future and achieve security peace of mind today.EXPLORE EI’S MANAGED SOC SERVICES

