Protecting Process Control Systems From Security Breaches
Photo by Adi Goldstein
Originally Posted On: Protecting Process Control Systems From Security Breaches (cornerstonecontrols.com)
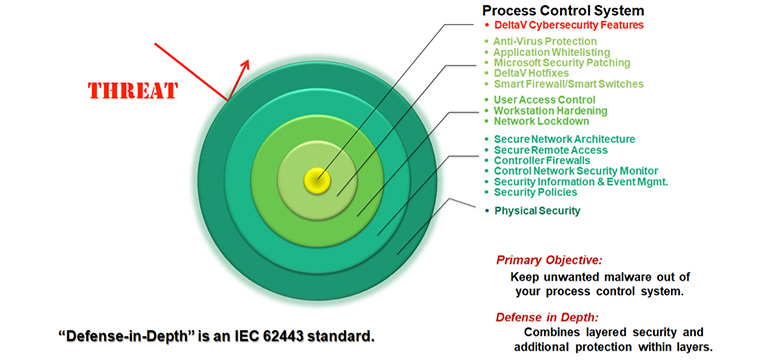
Traditionally network segmentation was a significant factor in the success of defense-in-depth cybersecurity strategies.
Control system networks were strongly segmented or isolated from other LANs on the site. Sites accomplished system segmentation by creating security zones and using security firewalls or other security devices to allow only authorized traffic between security zones (the zones and conduits model in the IEC 62443/ISA99 standard).
Today, control systems are increasingly adopting open standards and interoperable technologies to cater to this demand for operational analytics, served up by IIOT and other digital transformation technologies. Unfortunately, these standards also increase control systems’ vulnerability to electronic attacks and infections via the internet and other external and internal network intrusions.
Using OPC UA in a Defense-in-Depth Strategy
Communications security needs to become an enhanced component of an organization’s defense-in- depth strategy. The objective of communications security is to ensure only authorized applications can communicate with each other. Only valid messages are exchanged, and the integrity and confidentiality of messages exchanged between communicating applications are protected.
OPC UA (Open Protocol Communications Unified Architecture) is a sophisticated, scalable, and flexible mechanism for establishing secure connections between clients and servers. This unique technology for data transfer includes scalability, flexible address space, standard transports and encodings, security, internet capability, robust set of services, and certified interoperability.
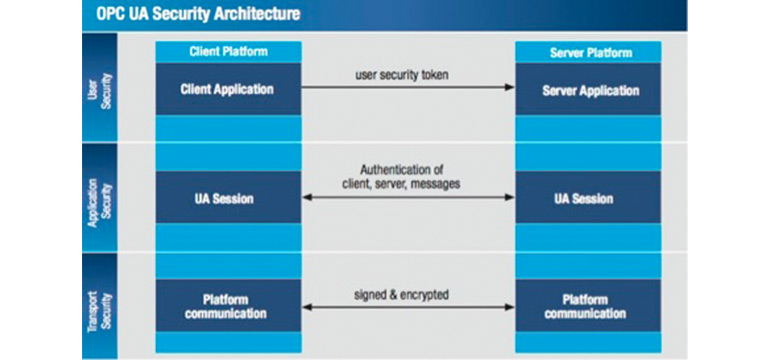
Figure 1.1 OPC UA Security Architecture
Source: OPC Connect (https://opcconnect.opcfoundation.org/2018/06/practical-security-guidelines-for-building-opc-ua-applications/)
OPC UA solves three main security goals:
- Provide a client-server authentication mechanism, thereby allowing the clients and back-office services to confirm who they are in the network.
- Secure user authentication so that only authorized users can configure clients and services in the network.
- Enforce integrity and authenticity of communications, preventing the intercepting and decoding of messages.
To achieve these goals, the OPC UA security model uses the following component options:
- Certificate-based authentication: this authentication method uses encryption to identify what computer or user is making a request positively, thus preventing and blocking “man-in-the-middle” attacks and requests from unauthorized sources. Certificate-based authentication is more secure than merely defining an access control list for the system based on components’ identification (e.g., IP address, hardware address).
- Authorization: OPC UA works within the facility’s overall security authorization infrastructure, allowing the site to determine how to manage those authorizations.
- Security Audit Trails: Audit trails provide traceability between client and server activities. Servers can implement event notifications to report auditable events to clients capable of processing and logging them.
- Message Confidentiality: OPC UA can use encryption to protect the confidentiality of messages exchanged by clients and servers.
- Integrity: To address integrity, OPC UA uses symmetric and asymmetric signatures.
The OPC UA server enforces security features, and OPC UA clients need to match the requirements to establish communications. We strongly recommend that you always use the security options to ensure the security and integrity of the data sent from and received by your control systems.
The following OPC UA Security Rules help to adhere to the security best practices when using OPC UA with control systems:
- Use Certificate Signing Request (CSR) to request a digital certificate from the Certificate Authority (CA) rather than using certificates exported with private keys.
- Do not export digital certificates, including their private keys.
- Use CA-issued digital certificates instead of self-signed certificates.
- Use ‘Sign and Encrypt’ security mode when configuring OPC UA within control systems. Default to the highest common denominator for the security policy, Basic256SHA256 preferably.
- Anonymous log-on is discouraged.
Even if using OPC UA to cross the gap between the control system and the enterprise network, OPC UA security is only one layer of the defense-in-depth strategy. Multiple security layers are always necessary to safeguard the entire network enterprise from numerous threats and security breach mechanisms. A formal security risk assessment is an excellent first step to determine if your defense-in-depth strategy is robust enough or adequately deployed.
